1.You need to design a backup strategy. You need to ensure that all servers are backed up every Friday night and a complete copy of all data is available with a single set of media. However, it should take minimal time to restore data. Which of the following would be the ____
Full
2.Your source data is of 50 GB. You make a full backup. Next week, once again you perform a full backup, but this time 10 more GB has been added to the source data. Second week, you perform another backup when the source backup has added 30 more GB. What is the total size of backups have you saved till date?
200 GB
3.You take a full backup of the source data on Monday. Rest of the week, you take differential backups. What would the differential backup of Friday contain?
Changes since the full backup
4.When restoring a backup, which of them is likely to be most time consuming to restore?
Incremental
5.You are asked to monitor a network which has a network monitoring system. Using the monitoring server, you notice that it is listening on port number 161 for network events. Which network monitoring protocol is in use?
SNMP
6.Refer to the following statements. Within the operation of the SNMP protocol, which of the following describes a MIB correctly?
1.a database used for managing the entities in a communications network
2.it has a hierarchical structure
3.provides connectivity via SQL database queries and web interface capabilities
Statements 1 and 2
7.You have added a new device to the network management application. What else should you add to the network management application to be able to control it?
MIB
8.A network administrator is implementing a ping from one end of the network to the other, records the average round-trip time and archives the results. What is most likely being prepared?
Network performance baseline
9.What kind of information would you expect to find within a network device’s event log? [Choose all that apply].
.Event descriptions
.Time of events
10.Employees are complaining that the network seems to be slow. How could you quantitatively determine if this is the case?
Compare network performance to baselines
11.To reduce any kind of network congestion bottleneck, you have configured client-side caching. Which of the following is likely to use this configuration?
Offline folders
12.You want to monitor the routers for their performance. In case of a performance bottleneck, you need to be alarmed. Which of the following protocol should you use?
SNMP
13.Refer to the exhibit. Which of the following configuration is being displayed?
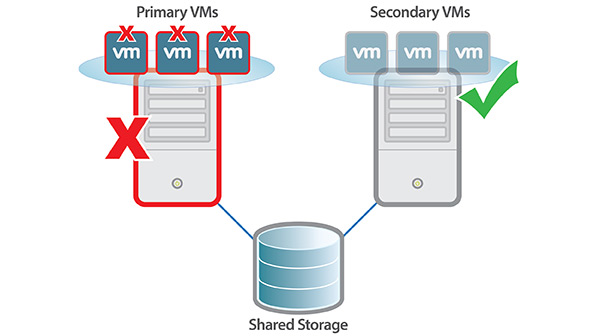
Fault tolerance
14.Which of the following is true about Load balancing on a network?
1) Provides redundancy
2) Provides an increase in throughput
3) Increases CPU resources
Statements 1 and 2 are true
15.Which power backup method will continually provide power to a server if the power goes out during a thunderstorm?
Online UPS
16.Which of the following features of a network connection between a switch and server is not improved by link aggregation?
Speed
17.What field in an IPv4 packet is altered to prioritize video streaming traffic over web surfing traffic?
DiffServ
18.What port do SNMP agents listen on?
Port 161
19.Your roommate has been hogging the bandwidth on your router lately. What feature should you configure on the router to limit the amount of bandwidth his computer can utilize at any one time?
Traffic shaping
20.What command requests the next record in an SNMP log?
SNMP Get Next
21.When shopping for a new router, what does the MTBF tell you?
How long devices like this one will last on average until the next failure
22.While troubleshooting a recurring problem on your network, you will want to examine the TCP messages being exchanged between a server and a client. Which tool should you use?
Wireshark
23.One of your coworkers downloaded several, very large video files for a special project she’s working on for a new client. When you run your network monitor later this afternoon, what list will your coworker’s computer likely show up on?
Top listeners
24.Which type of disaster recovery site contains all the equipment you would need to get up and running again after a disaster, and yet would require several weeks to implement?
Cold site
25.You have configured a new DHCP server and connected it to the network. There is connectivity to the server, but the clients in the network are unable to obtain IP addresses from the server. Which of the following enabled feature on the switch can cause this issue?
DHCP Snooping
26.You work in an organization as a network administrator. One of your new clients owns a hotel and has asked you to provide a single Internet connection for every room, but also ensure that the users are not visible to each other. Which technology on the switch will you use to meet the requirements stated in the scenario?
Create Private VLANs
27.You have empty ports on your switches, that is, no connected hosts. Which of the following are best practices to ensure that the empty ports are secure?
Move the ports from the default VLAN to a new, unused VLAN and then disable them
28.Which of the following versions of SNMP are considered unsecure? [Choose all that apply]
.SNMPv2c
.SNMPv1
29.You need to create an access list on your router to filter specific IP addresses and ports. You created entries with permit statements and deny statements. But you forget to add one specific deny statement to filter traffic from host A. How will this traffic be treated?
Host A traffic will be denied because, at the end of every access list, there is an implicit deny statement
30.You work as a network administrator in an organization. The company has three locations. A user is unable to access a shared folder located on a desktop in another location. You try to ping the IP address of the desktop, but it fails. You are unable to ping any IP address from that subnet. What is the next step you should perform on your router?
Check the IP routing table
31.You have two users who work on the same floor and belong to the same department. The organization has strict rules implemented for printer access. One of the users is unable to access the printer but has access to the Internet. What should you check on your switch?
VLAN assignment
32.You have implemented your network with new managed switches. A user is experiencing periodical interruptions on the network. While pinging the main server, you notice that there is periodical packet loss. What could cause this problem?
Broadcast storm
33.You have configured a new web server in your network, which will be used only from the local network. You published the website on TCP port 8443 but are unable to access the website on that port from a client device. You are able to ping the server IP address and also have access to the server using a Remote Desktop Connection. What could be the cause of this issue?
Windows firewall is enabled, and port 8443 is not allowing traffic
34.You have a complex network environment and have issues related to the routing of network traffic between hosts. Which of the following command will you use to troubleshoot this issue and verify how the packets are routed?
traceroute
35.You need to design a backup strategy. You need to ensure that all servers are backed up every Friday night and a complete copy of all data is available with a single set of media. However, it should take minimal time to restore data. Which of the following would be the ____
Full
36.Your source data is of 50 GB. You make a full backup. Next week, once again you perform a full backup, but this time 10 more GB has been added to the source data. Second week, you perform another backup when the source backup has added 30 more GB. What is the total size of backups have you saved till date?
200GB
37.You take a full backup of the source data on Monday. Rest of the week, you take differential backups. What would the differential backup of Friday contain?
Changes since the full backup
38.When restoring a backup, which of them is likely to be most time consuming to restore?
Incremental
39.You are asked to monitor a network which has a network monitoring system. Using the monitoring server, you notice that it is listening on port number 161 for network events. Which network monitoring protocol is in use?
SNMP
40.Refer to the following statements. Within the operation of the SNMP protocol, which of the following describes a MIB correctly?
1.a database used for managing the entities in a communications network
2.it has a hierarchical structure
3.provides connectivity via SQL database queries and web interface capabilities
Statements 1 and 2
41.You have added a new device to the network management application. What else should you add to the network management application to be able to control it?
MIB
42.A network administrator is implementing a ping from one end of the network to the other, records the average round-trip time and archives the results. What is most likely being prepared?
Network performance baseline
43.What kind of information would you expect to find within a network device’s event log? [Choose all that apply].
Event descriptions
Time of events
44.Employees are complaining that the network seems to be slow. How could you quantitatively determine if this is the case?
Compare network performance to baselines
45.To reduce any kind of network congestion bottleneck, you have configured client-side caching. Which of the following is likely to use this configuration?
Offline folders
46.You want to monitor the routers for their performance. In case of a performance bottleneck, you need to be alarmed. Which of the following protocol should you use?
SNMP
47.Refer to the exhibit. Which of the following configuration is being displayed?
Fault tolerance
48.Which of the following is true about Load balancing on a network?
1) Provides redundancy
2) Provides an increase in throughput
3) Increases CPU resources
Statements 1 and 2 are true
49.Which power backup method will continually provide power to a server if the power goes out during a thunderstorm?
Online UPS
50.Which of the following features of a network connection between a switch and server is not improved by link aggregation?
Speed
51.What field in an IPv4 packet is altered to prioritize video streaming traffic over web surfing traffic?
DiffServ
52.What port do SNMP agents listen on?
Port 161
53.Your roommate has been hogging the bandwidth on your router lately. What feature should you configure on the router to limit the amount of bandwidth his computer can utilize at any one time?
Traffic shaping
54.What command requests the next record in an SNMP log?
SNMP Get Next
55.When shopping for a new router, what does the MTBF tell you?
How long devices like this one will last on average until the next failure
56.While troubleshooting a recurring problem on your network, you will want to examine the TCP messages being exchanged between a server and a client. Which tool should you use?
Wireshark
57.One of your coworkers downloaded several, very large video files for a special project she’s working on for a new client. When you run your network monitor later this afternoon, what list will your coworker’s computer likely show up on?
Top listeners
58.Which type of disaster recovery site contains all the equipment you would need to get up and running again after a disaster, and yet would require several weeks to implement?
Cold site
59.At what layer of the OSI model do proxy servers operate?
Layer 7
60.Which of the following criteria can a packet-filtering firewall not use to determine whether to accept or deny traffic?
Application data
61.Who is responsible for the security of hardware on which a public cloud runs?
The cloud provider
62.Which of the following is not one of the AAA services provided by RADIUS and TACACS+?
Administration
63.Which device would allow an attacker to make network clients use an illegitimate default gateway?
DHCP server
64.Active Directory and 389 Directory Server are both compatible with which directory access protocol?
LDAP
65.What information in a transmitted message might an IDS use to identify network threats?
Signature
66.Which policy ensures messages are discarded when they don’t match a specific firewall rule?
Implicit deny
67.Which of the following ACL commands would permit web-browsing traffic from any IP address to any IP address?
access-list acl_2 permit https any any
68.Which principle ensures auditing processes are managed by someone other than the employees whose activities are being audited?
Separation of duties
69.You have configured a new DHCP server and connected it to the network. There is connectivity to the server, but the clients in the network are unable to obtain IP addresses from the server. Which of the following enabled feature on the switch can cause this issue?
DHCP Snooping
70.You work in an organization as a network administrator. One of your new clients owns a hotel and has asked you to provide a single Internet connection for every room, but also ensure that the users are not visible to each other. Which technology on the switch will you use to meet the requirements stated in the scenario?
Create Private VLANs
71.You have empty ports on your switches, that is, no connected hosts. Which of the following are best practices to ensure that the empty ports are secure?
Move the ports from the default VLAN to a new, unused VLAN and then disable them
72.Which of the following versions of SNMP are considered unsecure? [Choose all that apply]
.SNMPv2c
.SNMPv1
73.You need to create an access list on your router to filter specific IP addresses and ports. You created entries with permit statements and deny statements. But you forget to add one specific deny statement to filter traffic from host A. How will this traffic be treated?
Host A traffic will be denied because, at the end of every access list, there is an implicit deny statement
74.You work as a network administrator in an organization. The company has three locations. A user is unable to access a shared folder located on a desktop in another location. You try to ping the IP address of the desktop, but it fails. You are unable to ping any IP address from that subnet. What is the next step you should perform on your router?
Check the IP routing table
75.You have two users who work on the same floor and belong to the same department. The organization has strict rules implemented for printer access. One of the users is unable to access the printer but has access to the Internet. What should you check on your switch?
VLAN assignment
76.You have implemented your network with new managed switches. A user is experiencing periodical interruptions on the network. While pinging the main server, you notice that there is periodical packet loss. What could cause this problem?
Broadcast storm
77.You have configured a new web server in your network, which will be used only from the local network. You published the website on TCP port 8443 but are unable to access the website on that port from a client device. You are able to ping the server IP address and also have access to the server using a Remote Desktop Connection. What could be the cause of this issue?
Windows firewall is enabled, and port 8443 is not allowing traffic
78.You have a complex network environment and have issues related to the routing of network traffic between hosts. Which of the following command will you use to troubleshoot this issue and verify how the packets are routed?
traceroute
79.Which of the following is considered a secure protocol?
SSH
80.Leading up to the year 2000, many people expected computer systems the world over to fail when clocks turned the date to January 1, 2000. What type of threat was this?
Logic bomb
81.A company wants to have its employees sign a document that details some project-related information that should not be discussed outside the project’s team members. What type of document should they use?
NDA
82.Which type of DoS attack orchestrates an attack using uninfected computers?
DRDoS (Distributed Reflection DoS) attack
83.A former employee discovers six months after he starts work at a new company that his account credentials still give him access to his old company’s servers. He demonstrates his access to several friends to brag about his cleverness and talk badly about the company. What kind of attack is this?
Insider threat
84.A company accidentally sends a newsletter with a mistyped website address. The address points to a website that has been spoofed by hackers to collect information from people who make the same typo. What kind of attack is this?
Phishing
85.Your organization has just approved a special budget for a network security upgrade. What procedure should you conduct to make recommendations for the upgrade priorities?
Posture assessment
86.A spoofed DNS record spreads to other DNS servers. What is this attack called?
DNS poisoning
87.What kind of attack simulation detects vulnerabilities and attempts to exploit them?
Penetration testing
88.Which of these attacks is a form of Wi-Fi DoS attack?
Deauthentication attack
89.Which of the following is not one of the three AAA services provided by RADIUS and TACACS+?
Access control
90.What kind of firewall blocks traffic based on application data contained within the packets?
Content-filtering firewall
91.Which of the following features is common to both an NGFW and traditional firewalls?
User authentication
92.What feature of Windows Server allows for agentless authentication?
AD (Active Directory)
93.What software might be installed on a device to authenticate it to the network?
Agent
94.Which of the following ACL commands would permit web-browsing traffic from any IP address to any IP address?
access-list acl_2 permit http any any
95.Which command on an Arista switch would require an SNMP notification when too many devices try to connect to a port?
switchport port-security
96.Which NGFW feature allows a network admin to restrict traffic generated by a specific game?
Application awareness
97.Active Directory and 389 Directory Server are both compatible with which directory access protocol?
LDAP
98.At what layer of the OSI model do proxy servers operate?
Layer 7
99.Your organization has just approved a special budget for a network security upgrade. What procedure should you conduct to develop your recommendations for the upgrade priorities?
Posture assessment
100.Which type of DoS attack orchestrates an attack bounced off uninfected computers?
DRDoS attack
101.A company accidentally sends a newsletter with a mistyped website address. The address points to a website that has been spoofed by hackers to collect information from people who make the same typo. What kind of attack is this?
Phishing
102.A former employee discovers six months after he starts work at a new company that his account credentials still give him access to his old company’s servers. He demonstrates his access to several friends to brag about his cleverness and talk badly about the company. What kind of attack is this?
Insider threat
103.You need to securely store handheld radios for your network technicians to take with them when they’re troubleshooting problems around your campus network. What’s the best way to store these radios so all your techs can get to them and so you can track who has the radios?
Smart locker
104.Leading up to the year 2000, many people expected computer systems the world over to fail when clocks turned the date to January 1, 2000. What type of threat was this?
Logic bomb
105.Which of the following is considered a secure protocol?
SSH
106.A company wants to have its employees sign a document that details some project-related information that should not be discussed outside the project’s team members. What type of document should they use?
NDA
107.What type of attack relies on spoofing?
Deauth attack
108.What does the acronym CIA stand for in relation to network security? [Choose all that apply]
.Confidentiality
.Integrity
.Availability
109.Which threat actor will have prior knowledge of the network layout to perform a malicious attack?
Disgruntled network administrator
110.What is the purpose of Role-based Access Control (RABC)?
Users only have access to specific resources according to their job role
111.Where in a network segment will the DMZ be located?
Between the internal and external network
112.Which of the following can be used for multi-factor authentication? [Choose all that apply]
.Smart Card
.Username and Password
113.You have recently upgraded your network. Which method will help you to track its improvements to ensure accurate comparison of the performance?
Baseline review
114.You have been using a wireless router at home. You get an E-mail from the manufacturer that the same router now has been provided with new functionality in its admin interface. You want to get this functionality on the same router without losing existing configuration. What should you do with minimum administrative effort?
Upgrade the firmware on the wireless router
115.You have recently shared a document with the user that mentions the need and set of rules for creating credentials of appropriate complexity. Which document is this?
Password policy
116.A password policy as part of a network user agreement may require users to do which of the following? [Choose all that apply].
.Require a minimum number of characters
.Require at least one of different kinds of characters (numbers, capital letters)
117.Why would an attacker perform a brute force attack?
To gain access to a password protected system
118.Which of the following commands do you need to run in order to scan the PLABWIN10 devices?
mbsacli /target 192.168.0.5 > reports.txt
119.From the MBSA scan performed in Task 3, how many users have non-expiring passwords?
3 of 4
120.After performing the MBSA scan from the Command Line in task 4, how many user accounts have blank or simple passwords?
2 of 4
121.When executing the mbsacli command, what does the /r function perform?
Scans a range of IP Addresses
122.Your organization’s network has multiple layers of security devices. When you attempt to connect to a service on the Internet. However, you receive a security message from the operating system stating that this service is blocked on your workstation. What could be the probable cause?
The host-based firewall settings are blocking the service.
121.Refer to the exhibit. Which of the following networking device is being shown in the middle in red color?
UTM appliance
123.Which of the following are characteristics of the MTU when applied to IP and Ethernet networks? [Choose all that apply.]
.The MTU is the largest size an encapsulated segment can have
.The default MTU is 1500 bytes
124.Your network comprises of multiple switches and a single router. Currently, all users of finance and marketing on the third floor are connected to a flat switch. You must segregate traffic between your finance and marketing groups. You need to ensure that critical finance information can flow without delay to the finance users and ensure additional level of security. What should you do?
Configure VLANs on the switch
125.When a switch receives data on one of its ports, what is the next step does it perform?
Checks the MAC table for the destination system
126.Identify the correct statement for a switch’s MAC Address Table.
It is possible to have more than one MAC address corresponding to a single port.
It is possible to have more than one port corresponding to a single MAC address.
The first is true, the second is false
127.While examining frames on the network using a packet analyzer, you observe several frames that are double tagged. What kind of attack could a host on the network be performing that may result in this?
VLAN hopping
128.Which of the following IP network configuration elements a DHCP server, running on Windows Server 2012, can provide to a Windows 10 system? [Choose all that apply.]
.Subnet mask
.IPv4 address
129.Refer to the exhibit. Which of the following type of attack is being depicted?
ARP poisoning
130.Which of the following can be prevented if DHCP snooping is implemented on a switch? [Choose all that apply].
.Preventing the rogue DHCP servers
.Preventing the malformed DHCP traffic
131.Which OSI layer is responsible for directing data from one LAN to another?
Network layer
132.What kind of route is created when a network administrator configures a router to use a specific path between nodes?
Static route
133.When a router can’t determine a path to a message’s destination, where does it send the message?
Gateway of last resort
134.A routing protocol’s reliability and priority are rated by what measurement?
AD
135.Which routing protocol does an edge router use to collect data to build its routing tables for paths across the Internet?
BGP
136.What is the lowest layer of the OSI model at which LANs and WANs support the same protocols?
Layer 3
137.What kind of device can monitor a connection at the demarc but cannot interpret data?
Smartjack
138.What specifications define the standards for cable broadband?
DOCSIS
139.What method does a GSM network use to separate data on a channel?
TDMA
140.Which of these cellular technologies offers the fastest speeds?
LTE-A
141.Refer to the exhibit. Which authentication protocol is shown in this exhibit?
TACACS+
142.Which of the following types of authentication and access control does not need an external AAA server to verify credentials inputted by users?
Local authentication
143.Which of the following types of authentication will continue to function even if network connectivity to any available AAA servers is lost?
Local authentication
144.What kind of network is the PSTN?
Circuit-switched
145.What kind of device can monitor a connection at the demarc but cannot interpret data?
Smart jack
146.Where does an MPLS label go in a PDU?
Between Layers 2 and 3
147.What is the lowest layer of the OSI model at which LANs and WANs support the same protocols?
Layer 3
148.How many channels are in an ISDN PRI connection?
23B+D
149.What method does a GSM network use to separate data on a channel?
TDMA
150.Which DSL standard has the fastest speeds immediately outside the CO?
VDSL
151.An organization can lease a private _________________ that is not shared with other users, or a _________________ that can be physically configured over shared lines in the carrier’s cloud.
dedicated line, virtual circuit
152.______________ in SONET are analogous to the ________________ of T-carriers.
OC levels, digital signal levels
153.What specifications define the standards for cable broadband?
DOCSIS
154.Which type of address uses 12 hexadecimal digits? (Choose two.)
.MAC address
.Physical address
155.Which of the following is the PDU used by a connection-oriented Transport layer protocol?
Segments
156.Which cell phone technology uses a spread-spectrum technique that uses codes on the packets to keep calls separated?
CDMA
157.You need to implement software that can manage virtual machines and manage resource sharing between a host computer and guest VMs. What should you implement?
A hypervisor
158.A network administrator has been tasked with configuring access to the Internet for about 50 computers. The administrator has been told that all Internet access should go through a single computer so incoming and outgoing traffic can be screened and only that computer should have an address revealed to the Internet. What should the administrator set up?
Proxy server
159.After configuring a static IP address on a desktop computer, the technician finds that he cannot communicate with other devices on the LAN. He verifies that the IP address and subnet mask are in the correct IP subnet. While the technician is troubleshooting, another user complains that she can no longer access the network. No other users seem to be having any problems. What could be the cause of the problem?
Duplicate IP
160.Which of the following best describes the IEEE 802.11b standard?
2.4 GHz, 11 Mbps
161.Which authentication protocol uses PKI to provide mutual authentication?
EAP-TLS
162.The Webmaster for a company installed a certificate on a Web server to provide secure communication between the Web server and Web browsers. What protocol will be used to provide a secure channel?
SSL
163.A website has recently seen a spike in activity due to a recent marketing campaign that has caused a decrease in performance. The operators want to improve performance to their website. What should they implement?
Load balancing
164.Your company is using standard structuring cabling techniques. You need a spreadsheet created that tells you which switch port in the IDF each PC is plugged into. Which of the following will help you with this task? (Choose two.)
.Patch panel labeling
.Wall jack labeling
165.You have been asked to install a physical security control that will prevent unauthorized users from accessing the server room. Which of the following should you install?
Proximity reader
166.Which protocol is most likely used to communicate with a SAN over an Ethernet LAN using standard NICs?
iSCSI
167.You are a network administrator for a company that has two buildings. You are setting up a wireless network so users can maintain a network connection as they move between buildings. What should you be sure to configure on your WAPs to give the wireless users the best mobile experience?
Set the SSIDs to match
168.A company negotiates with a service provider for Frame Relay service. At the conclusion, the company and service provider sign an agreement specifying the bandwidth and the availability of the service. What document was signed?
SLA
169.You have been called to terminate a DS3 connection at a customer site. What type of connector should you bring to terminate the copper cable?
BNC
170.Which type of Internet connection can provide an unshared connection over regular telephone lines operating with at least 1 Mbps of bandwidth?
DSL
171.One of your clients is adding several computers to a guest waiting area. They have asked you to ensure that inappropriate websites cannot be accessed from those computers. What should you configure?
Content filter
172.A technician has run an MMF cable from the IDF to the MDF and is not getting a strong signal. He needs to check the length of the cable and see if there are any breaks or mismatched connectors. What should he use?
OTDR
173.When two or more WAPs are installed in close proximity, what must be different on each WAP to avoid problems?
Channel
174.A man receives a fraudulent email from his bank asking him to confirm his user name and password by going to a particular website. What has occurred?
Phishing attack
175.Which of the following is a private IP address?
172.30.99.8
176.Your boss has asked you to run an Nmap scan on all the routers on one of your subnets. What is your boss looking for?
Open ports
177.One morning you come into work and find that one of your servers has been attacked by malware. All the security patches are up-to-date. After doing some investigating and research, you cannot find any information about the nature of the attack or the server vulnerability that allowed it. What are you most likely experiencing?
Zero-day exploit
178.MMF cable runs from a company datacenter to a workgroup switch that has 16 RJ-45 ports. A connection must be made from the MMF cable to the switch. What is necessary?
Media converter
179.Which of the following is found in the intermediate distribution frame and is used to terminate cabling coming from the work area?
Patch panel
180.You need to ensure that customers have access to your public web servers in the event of a disaster such as a power outage or a failed server. What do you need to implement on your network?
High availability
181.You have been asked to install a device that supports WPA2 and 802.11ac. What device should you install?
WAP
182.While investigating a problem with a router, the show interface command reports line protocol down on the Ethernet port. A Cat5e cable is plugged into the port and is connected to another router’s Ethernet port about 80 meters down the hall. Both routers are turned on and configured correctly. The cable is terminated using the TIA/EIA 568A standard on both ends and was tested with a cable certifier. What would solve the problem?
Re-terminate one end using TIA/EIA 568B
183.A network administrator manages a network with 75 servers. At least twenty of those servers are approaching end of life but the applications they are running are still critical. The administrator wants to consolidate the older servers into about five servers while maintaining isolation among the applications. What should the administrator implement?
Server virtualization
184.A network technician has been asked to make a connection between two switches in an IDF and MDF using 1000BaseSX Ethernet. The IDF and MDF are about 85 meters apart. The technician brings an adequate length of Cat6a cable to make the connection but finds that he is unable to make a connection. What is the problem?
He needs a multimode fiber cable
185.You are planning to configure a voice and video system that will use TCP/IP. You need to study the protocols and devices you might be using to deploy the system. Which of the following are you likely to study? (Choose two.)
.SIP
.H.323
186.A user is unable to connect to a server with address 172.21.100.100. A technician troubleshooting the problem enters the ipconfig command and sees the output shown below. What should be done to resolve the problem?
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::ec42:7e6a:d2d4:5410%20
IPv4 Address. . . . . . . . . . . : 172.31.210.1
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 172.31.10.250
Change the default gateway to 172.31.210.250
187.Three Cat 5e cables were run from an office area to three computers in a machine shop. Work took place on the weekend when the machine shop was closed. The network is using 1000BaseT switches and all the NICs are 1000BaseT compatible. The longest run of cable is 85 meters. All cabling was certified and network connectivity was verified. On Monday, the users of the computers report very slow network performance and the switch reports CRC errors. What is the most likely reason for the problems?
External EMI/RFI
188.Which type of cable should you use if you need to support up to 10 Gbps bandwidth at a distance of 85 meters using RJ45 connectors?
Cat 6a
189.A recent audit has prompted a lengthy search for the whereabouts of high-value equipment. While the equipment was eventually found, you want to ensure that you don’t have to waste time in the future searching for your equipment. What can you put in place to keep track of your equipment?
Asset tracking
190.Which device uses CSMA/CD when the interface is set to half duplex mode?
Ethernet NIC
191.You want to implement a system that uses certificates for identity verification and secure key management. What type of system do you need to implement?
PKI
192.Which of the following works over two copper wire pairs, uses TDM, and transmits at 1.544 Mbps?
T1
193.You are configuring some new network printers and you want to be sure the printers are always dynamically assigned the same IP address. What should you configure?
DHCP reservation
194.One of your clients has opened a branch office in another state. Both the main office and the new branch office have fast, reliable Internet access. You have been asked to connect the branch office with the main office with a secure connection that uses their existing network infrastructure. What do you recommend?
Site-to-site VPN
195.You are about to deploy a new server that will contain sensitive data about your clients. You want to test the server to look for problems that might allow an attacker to gain unauthorized access to the server. This testing should not attempt to exploit weaknesses, only report them. What type of test should you perform?
Vulnerability scan
196.Which layer of the OSI model should you examine if you want to troubleshoot a problem with the HTTP protocol?
Application
197.You are familiar with SSH and are happy with the level of security it provides. You want similar secure communication for file transfers on your network. What should you use?
SFTP
198.Which TCP/IP protocol has only these fields in its header: Source port, Destination port, Length, and Checksum?
UDP
199.A company has a website that has seen a large increase in visitors and they are concerned that if the trend continues, the web server’s performance will be compromised. You have been asked to help solve this problem without having to replace the current server. What can you do?
Install a second server and load balancer
200.You need to perform out-of-band management on a router. How should you connect to the router?
Via the console port
201.Which device is used to detect suspicious packets and provides information about possible violations to a management station?
IDS
202.Several users on the second floor of your company’s building are reporting that the network is down. You go to the second floor to investigate and find that you are able to access the network. What troubleshooting step should you take next?
Question users
203.Which technology allows multiple signals to travel simultaneously over one medium?
Multiplexing
204.A user transfers several MP3 files from her smartphone to her laptop computer using Bluetooth. What type of network infrastructure is she using?
PAN
205.You have been tasked with hardening some of the routers and switches on your network. Currently, your network administrators use telnet to remotely manage the devices. What can you do to make those devices more secure?
Use SSH for remote management instead of telnet
206.What type of connector is used with an SFP port?
LC
207.A network technician is meeting with a representative of an ISP to inspect the facility where a new WAN connection will be made. Where should the technician meet the representative?
MDF
208.Which device should you install that will give your mobile users secure remote access to the company servers through the public Internet?
VPN concentrator
209.You have been asked to examine the status of antivirus software, security patches, and open ports. When you are finished, you should provide a report of your findings. What have you been asked to perform?
Posture assessment
210.Recent police reports suggest that unsavory individuals have been casing the neighborhood where your company is located. You want to ensure that an alarm is triggered in the event someone is detected roaming the premises after business hours. What are you most likely to deploy?
Motion detection
211.Which of the following is a valid example of an IPv6 link local address?
FE80::1
212.A technician is installing RG6 cable and asks you to retrieve a connector from the parts drawer. What type of connector do you need?
F-connector
213.Which networking model should you use to allow the users on each computer to control access to their own shared folders and printers without centralized control?
Peer-to-peer
214.A network technician is asked to send ICMPv6 packets to the IPv6 loopback address on her computer. What command will the technician use?
ping ::1
215.While installing routers between two buildings, a technician must configure an IPv4 address on both routers using a subnet mask that will yield only the required IP addresses. What should the technician use for the subnet mask, expressed in CIDR notation?
/30
216.You have recently implemented a new WAN technology to connect a remote branch office to your headquarters. While making VoIP calls between the offices, employees complain about delays between someone talking and the other party hearing what they’ve said. Which WAN technology is most likely to cause this apparent latency?
Satellite
217.Which of the following is an authentication protocol that encrypts the username, authorization, and accounting information, works only over TCP, and was developed by Cisco?
TACACS+
218.You are investigating a problem between two wireless bridges and you find that signal strength is lower than expected. Which of the following could cause the problem?
Wrong antenna type
219.You are going to be installing a videoconferencing system. One of the requirements of the system is that only workstations that run the conferencing client application receive packets related to the videoconference. You need to assign an address to the videoconferencing application. Which of the following addresses is appropriate?
229.1.100.1
220.You have just finished configuring a router on your corporate network that consists of several subnets. Some users have informed you that they have access to some of the servers, but not others that they used to have access to. What is the most likely reason for this problem?
Access control lists
221.Which of the following devices works with frames and MAC addresses and supports STP?
Switch
222.You have recently set up a new Windows server and have configured the Administrator account with a strong password. What else should you do to make the new server more secure?
Rename the Administrator account
223.A network administrator wants to provide backup power for his datacenter. He will be using a generator. What type of power does a generator produce and what other component is needed to provide the type of power required for a datacenter?
Produces DC power, need an inverter
224.Which of the following separates multiple signals on the same medium by using time slots where each time slot carries data to a different destination or carries a different type of data to the same destination?
TDM
225.You are planning on a redesign of your network that will involve adding two VLANs and reconfiguring some IP subnets. What should you do first?
Submit a change request document
226.A startup company has an idea for a new medical records application. The company wants to develop the application so it can be run on multiple OSs. However, they have limited funds to build the development environment that is necessary to create and test the application properly. What service should they consider?
Public PaaS
227.You are capturing packets with a network sniffer and notice a number of packets that are flagged by the sniffer and described as TCP retries. Which layer of the OSI model should you investigate?
Transport
228.A number of computers have been reported to be getting incorrect IP addresses. After doing some investigating, an unauthorized DHCP server has been determined to be the cause. Which step in the troubleshooting process should be performed next?
Establish a plan of action to find the DHCP server
229.You need to provide a method to ensure that sensitive files downloaded from your servers can be verified for integrity. Which of the following solutions can you deploy?
SHA-2
230.While interviewing a user that has reported trouble accessing a server, you determine that other users on the LAN have no problem accessing the server. What question should you ask next?
Can you access other devices on the network?
231.While cleaning loose-tube fiber-optic cables, a technician gets some of the cleaning solvent near his eyes. Which of the following should the technician check to see how to deal with the problem?
MSDS
232.You need to be able to create rules to filter packets and protect against attacks from the Internet. What type of device should you use?
Firewall
233.While setting up a new network, a technician connects two switches together using a Cat6 straight-through cable. The switch ports are configured for 1000BaseT Ethernet, full-duplex, and do not support auto-MDIX. After making the connection, the link status light for both ports remains off. What is the most likely problem?
Wrong cable termination
234.A network has four switches, each with twenty computers connected to the switch ports. Each set of twenty computers been assigned a different IP network number. What is required for all computers to communicate with each other?
Router
235.You are configuring an AP for a WLAN. You want to use the strongest encryption supported by the device. Which of the following should you choose?
WPA2
236.To improve performance on an iSCSI SAN, a network technician configured an MTU value of 9000 on the Ethernet LAN. What did the technician configure?
Jumbo frames
237.You arrive at a customer site to resolve a problem with a router. After logging on to the router, you find that it uses a different operating system than the routers you are familiar with. Which troubleshooting step should you take next?
Escalate the problem
238.A user’s computer is redirected to an attacker’s server after the attacker transmitted several frames onto the network. After some investigation, you have found that the user’s computer had an incorrect mapping of an IP address to a MAC address. What type of attack took place?
ARP cache poisoning
239.While using a protocol analyzer, you see a packet with UDP source port 68 and destination port 67. What are you seeing?
A DHCP packet going from the DHCP client to the DHCP server
240.You have been asked to install a WLAN for a small business. You centrally locate the WAP in a large room that contains about 15 cubicles where employees work with their mobile devices. You test connectivity from all locations and find that signal strength is good throughout the room. Several months later, you are called to troubleshoot connectivity problems at the site. You find that the large room was divided into two smaller rooms by a floor to ceiling wall with metal studs. What is the most likely reason for the connectivity problems?
Interference
241.You’ve arrived on site to a WAN installation where you will be performing maintenance operations. You have been told the WAN protocol in use allows multiple Layer 3 protocols and uses routers that use labels in the frame headers to make routing decisions. What WAN technology is in use?
MPLS
242.The default VLAN on a switch has been assigned an IP address of 172.19.0.64/27 with a default gateway of 172.19.0.94. You can’t ping the switch from your workstation that has the address 172.19.0.66/27 but you can ping your default gateway that has the address 172.19.0.94. Why can’t you ping the switch?
The switch has the wrong IP address
243.Which of the following is associated with SNMP software? (Choose two.)
MIB
Trap
244.You need to configure a voice VLAN on your Cisco switch with the VLAN ID 10. Which of the following command will you use on the global configuration mode?
configure terminal
vlan 10
name VOICE
245.What is the name of the switching feature that prevents frame dropping in case of congestion by pausing sending frames?
Flow control
246.You have a high speed environment in your network with speeds of up to 40 Gbps. Users in the network are experiencing slow performance issues on some applications. What do you need to enable on your equipment to improve the performance?
Jumbo frames
247.What is the key drawback of STP or per VLAN STP – PVST?
Slow convergence
248.You want to improve the security in your network and enable MAC address filtering. Which of the following feature will you configure on the switch ports?
Port security
249.In which type of cloud configuration is the customer responsible for maintaining the operating system and software?
Infrastructure as a Service (IaaS)
250.When choosing the location to create resources in the cloud, what is the best location for the resources? [Choose all that apply]
Geographically closest Cloud Service Provider Datacenter
Closest Regional Cloud Service Provider Datacenter
251.With a _________ Cloud, the hardware and software are maintained by the company that owns it.
Private
252.Which of the following is an example of Software as a Service (SaaS)? [Choose all that apply]
Dropbox
Microsoft 365
253.What is the advantage of elasticity when utilizing a cloud service provider? [Choose all that apply]
.Resources are deallocated when not used
.Resource allocation is scaled automatically
254.What software allows you to define VMs and manage resource allocation and sharing among VMs on a host computer?
Hypervisor
255.What virtual, logically defined device operates primarily at the data link layer to pass frames between nodes?
Virtual switch
256.Which device can manage traffic to multiple servers in a cluster so all servers equally share the traffic?
Load balancer
257.With which network connection type does the VM obtain IP addressing information from its host?
NAT mode
258.Which type of switch connects all devices in a rack to the rest of the network?
ToR switch
259.Which cloud service model gives software developers access to multiple platforms for testing code?
PaaS
260.When shopping for a new router, what does the MTBF tell you?
How long devices like this one will last on average until the next failure
261.What information does the switchport port-security command use to restrict access to a switch’s interface?
MAC address
262.Which of the following features of a network connection between a switch and server is not improved by link aggregation?
Speed
263.Which cloud management technique executes a series of tasks in a workflow?
Orchestration
264.Which tier in the three-tiered network is responsible for routing traffic in and out of a network?
Core
265.At which layer in Software Defined Network (SDN) will you find a firewall?
Application Layer
266.How many tiers are there in the spine and leaf network architecture?
2
267.The traffic that enters into a network is known as the ___________ traffic.
Southbound
268.Which storage area network (SAN) connection type uses an Ethernet switch to send commands to the SAN devices?
Internet Small Computer Systems Interface (iSCSI)
269.What is the purpose of implementing a DHCP server on a network? [Choose all that apply]
.Automatically assign a DNS server address to a host
.Dynamically allocate IP addresses to hosts on the network
270.After installation of the DHCP server role, why is it necessary to restart the DHCP service?
To ensure the credentials that were stipulated is applied
271.What is the functionality of a lease for a DHCP server?
It stipulates how long an IP address will be allocated to a host
272.When creating a scope on a DHCP server, what is the purpose of specifying an exclusion?
An exclusion is specified to ensure specific IP addresses are not automatically allocated to hosts
273.On which server will the DHCP server role normally be installed?
Domain Member Server
274.Which of the following is a Class C Private IP address?
192.168.0.10
275.What is the Subnet Mask for a Classful Class A IP range?
255.255.255.0
276.What would the subnet mask be of the following network range?
255.255.255.240
277.Which of the following is the Loopback address for IPv4?
127.0.0.1
278.What is the functionality of a Multicast IP address?
Sends network communication to a specific set of hosts
279.Which of the following Stratum Levels is the least Trusted?
Level 15
280.Which of the following command-line commands would display time sync information for an NTP client?
w32tm /query /peers
281.What is the maximum number of NTP Servers that an NTP client can be synchronized with?
1
282.Which of the following port is used by NTP Servers to provide time synchronization?
123
283.Which Transport Layer protocol is used by NTP Servers to provide time synchronization?
UDP
284.Which part of a MAC address is unique to each manufacturer?
The OUI
285.What type of device does a computer turn to when attempting to connect with a host with a known IP address on another network?
Default gateway
286.What decimal number corresponds to the binary number 11111111?
255
287.Suppose you send data to the 11111111 11111111 11111111 11111111 IP address on an IPv4 network. To which device(s) are you transmitting?
All devices on your local network
288.When your computer first joins an IPv6 LAN, what is the prefix of the IPv6 address the computer first configures for itself?
FE80::/64
289.If you are connected to a network that uses DHCP, and you need to terminate your Windows workstation’s DHCP lease, which command would you use?
ipconfig /release
290.You have just brought online a new secondary DNS server and notice your network-monitoring software reports a significant increase in network traffic. Which two hosts on your network are likely to be causing the increased traffic and why?
The secondary and primary DNS servers because the secondary server is requesting zone transfers from the primary server
291.Which type of DNS record identifies an email server?
MX record
292.Which of these commands has no parameters in Windows?
hostname
293.which DNS server offers the most current resolution to a DNS query?
Primary DNS server
294.What transport protocol/ports do DNS and DHCP use?
UDP 53 / UDP 67 and 68
295.You work as a network administrator and are responsible for configuring network firewalls, routers and switches. You have configured rules between the user and server VLANs. You received a request from your development team to create a new rule that allows port TCP 1433 to the database server. Based on the port number, which database is installed on the server.
SQL
296.You work as a network administrator in a domain environment. You have a new firewall and need to configure it. You are asked to create web filtering and firewall rules based on domain groups. Which of the following protocol will you use to integrate your firewall directly with Active Directory?
LDAP
297.To be able to remotely manage a Windows device securely, which of the following protocols can be used?
RDP
298.Which of the following connection methods can be used to connect a company’s offices which are located in different geographical areas?
Site-to-Site VPN
299.While configuring a new VPN client, which Role service needs to be installed for the Remote Access role on a Windows server?
Direct Access and VPN (RAS)
300.Which permission needs to be assigned to a user to be able to connect to a VPN connection?
Network Access permissions
Other Links:
See other websites for quiz:
Check on QUIZLET
